Signing documents online? Here’s what cybercriminals hope you’ll click next
By
Maan
- Replies 0
Digital convenience has revolutionised how we handle official documents—but not without new risks.
What appears to be a routine request to sign something electronically could, in fact, be a doorway for cybercriminals.
What follows is a closer look at how one popular platform has become a target—and what you need to know to stay safe.
Digital signing apps like Docusign have become a staple for businesses and individuals alike—but their popularity has made them a ripe target for cybercriminals.
While these tools have removed the hassle of printing, signing, scanning and emailing documents, they’ve also opened the door to sophisticated phishing attacks.
With over one billion users globally and a customer list that includes 95 per cent of the Fortune 500, Docusign had firmly landed in the sights of malicious actors.
Here’s how scammers have exploited its name—and what you and your workplace can do about it.
How scammers impersonated Docusign
Phishing remains one of the most dangerous cyber threats in circulation.
Verizon reported that 19 per cent of data breaches involved phishing as the initial access point, with 60 per cent containing a ‘human element’.
That makes widely trusted platforms like Docusign perfect bait.
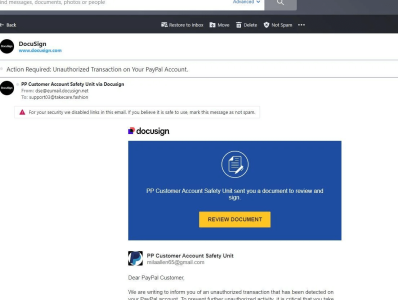
Typically, victims received a spoofed Docusign email—sometimes with an attachment or a QR code—urging them to click a bright yellow ‘review document’ button.
These links often redirected users to fake Microsoft login pages, where they were tricked into handing over credentials or financial details.
QR codes were particularly effective, as they were often scanned with mobile devices that lacked security software.
Once threat actors had access, they could move laterally within networks, escalate privileges and potentially install ransomware or exfiltrate sensitive data.
Common scams seen in recent months
These phishing campaigns varied in method and complexity.
1. Some cybercriminals registered actual Docusign accounts and used the platform’s API to send out legitimate-looking envelopes impersonating known brands.
2. Others posed as US government agencies, hoping to convince vendors to send payments to fake invoice accounts.
3. Many sent emails pretending to be HR or payroll departments, redirecting users to spoofed login pages.
4. There were refund scams, where a fake transaction notice encouraged victims to call a number—only to be pressured into handing over personal or banking information.
5. One popular scam even used Docusign branding to mimic supplier invoices and initiate fraudulent money transfers.
Screenshots of these tactics were widely shared on social media platforms like social media, revealing just how convincing the scams could appear.
How to reduce your risk
Prevention starts with awareness. Organisations were urged to update staff training and phishing simulations to include examples that mimicked Docusign emails.
Key red flags included:
Beyond training, technical measures could make a major difference.
Multi-factor authentication (MFA) should have been mandatory for all corporate accounts.
Password hygiene—including unique, strong passwords stored in password managers—was crucial.
Security tools from trusted vendors like ESET could detect malicious attachments, prevent access to phishing sites, and apply filtering rules.
Companies were advised to change internal processes to verify large fund transfers and encourage employees to forward all suspicious emails to IT/security teams and to [email protected].
What to do after a phishing incident
If someone fell for a Docusign-themed scam, quick action was essential.
1. The affected user’s passwords needed to be reset immediately, especially for any accounts sharing credentials.
2. Their device should be scanned for malware and isolated from the network.
3. Security teams had to monitor accounts and the dark web for signs of stolen data.
4. Forensics were often required to determine the extent of access and what the attackers were after.
5. The incident should be used as a learning opportunity, reinforcing reporting and vigilance across the team.
It’s not just a workplace risk
While Docusign was widely used by corporations, individuals were just as vulnerable—especially when buying property or completing tax paperwork.
Source: Youtube/CatfishedOnline
The same advice applied: avoid clicking links in emails, use the security code to access documents via the official Docusign site, and report anything suspicious.
Electronic signatures were undeniably convenient...but that convenience should never come at the cost of security.

With digital signing tools becoming a daily convenience, do you feel confident spotting a scam when it lands in your inbox? Let us know your thoughts in the comments.
What appears to be a routine request to sign something electronically could, in fact, be a doorway for cybercriminals.
What follows is a closer look at how one popular platform has become a target—and what you need to know to stay safe.
Digital signing apps like Docusign have become a staple for businesses and individuals alike—but their popularity has made them a ripe target for cybercriminals.
While these tools have removed the hassle of printing, signing, scanning and emailing documents, they’ve also opened the door to sophisticated phishing attacks.
With over one billion users globally and a customer list that includes 95 per cent of the Fortune 500, Docusign had firmly landed in the sights of malicious actors.
Here’s how scammers have exploited its name—and what you and your workplace can do about it.
How scammers impersonated Docusign
Phishing remains one of the most dangerous cyber threats in circulation.
Verizon reported that 19 per cent of data breaches involved phishing as the initial access point, with 60 per cent containing a ‘human element’.
That makes widely trusted platforms like Docusign perfect bait.
Typically, victims received a spoofed Docusign email—sometimes with an attachment or a QR code—urging them to click a bright yellow ‘review document’ button.
These links often redirected users to fake Microsoft login pages, where they were tricked into handing over credentials or financial details.
QR codes were particularly effective, as they were often scanned with mobile devices that lacked security software.
Once threat actors had access, they could move laterally within networks, escalate privileges and potentially install ransomware or exfiltrate sensitive data.
Common scams seen in recent months
These phishing campaigns varied in method and complexity.
1. Some cybercriminals registered actual Docusign accounts and used the platform’s API to send out legitimate-looking envelopes impersonating known brands.
2. Others posed as US government agencies, hoping to convince vendors to send payments to fake invoice accounts.
3. Many sent emails pretending to be HR or payroll departments, redirecting users to spoofed login pages.
4. There were refund scams, where a fake transaction notice encouraged victims to call a number—only to be pressured into handing over personal or banking information.
5. One popular scam even used Docusign branding to mimic supplier invoices and initiate fraudulent money transfers.
Screenshots of these tactics were widely shared on social media platforms like social media, revealing just how convincing the scams could appear.
How to reduce your risk
Prevention starts with awareness. Organisations were urged to update staff training and phishing simulations to include examples that mimicked Docusign emails.
Key red flags included:
- Mismatched sender names and email addresses
- Spelling or grammatical errors
- Attachments in an initial Docusign message (which should never happen)
- Security codes missing from emails (legitimate Docusign documents include these)
- Suspicious links or URLs, which users should check by hovering over before clicking
Beyond training, technical measures could make a major difference.
Multi-factor authentication (MFA) should have been mandatory for all corporate accounts.
Password hygiene—including unique, strong passwords stored in password managers—was crucial.
Security tools from trusted vendors like ESET could detect malicious attachments, prevent access to phishing sites, and apply filtering rules.
Companies were advised to change internal processes to verify large fund transfers and encourage employees to forward all suspicious emails to IT/security teams and to [email protected].
What to do after a phishing incident
If someone fell for a Docusign-themed scam, quick action was essential.
1. The affected user’s passwords needed to be reset immediately, especially for any accounts sharing credentials.
2. Their device should be scanned for malware and isolated from the network.
3. Security teams had to monitor accounts and the dark web for signs of stolen data.
4. Forensics were often required to determine the extent of access and what the attackers were after.
5. The incident should be used as a learning opportunity, reinforcing reporting and vigilance across the team.
It’s not just a workplace risk
While Docusign was widely used by corporations, individuals were just as vulnerable—especially when buying property or completing tax paperwork.
Source: Youtube/CatfishedOnline
The same advice applied: avoid clicking links in emails, use the security code to access documents via the official Docusign site, and report anything suspicious.
Electronic signatures were undeniably convenient...but that convenience should never come at the cost of security.
Key Takeaways
- Scammers spoofed trusted platforms like Docusign to launch phishing attacks using fake emails and QR codes.
- Cybercriminals used tactics like fake invoices, refund scams and impersonation of agencies to trick victims.
- Organisations were urged to train staff, enable MFA, use security tools and report suspicious messages.
- Victims needed to reset passwords, isolate infected devices, and investigate breaches to prevent further damage.
With digital signing tools becoming a daily convenience, do you feel confident spotting a scam when it lands in your inbox? Let us know your thoughts in the comments.