Are you at risk? Over 100k business accounts fall victim to Facebook Messenger phishing each week
We’re all accustomed to a few spam messages here and there on Facebook Messenger, but it’s a different ballgame when criminals are sending out messages with malicious intent.
This is exactly what hackers have been doing, according to a worrying report from Guardio Labs. They’re using massive phishing networks and fake and/or compromised Facebook accounts to target vulnerable business owners via Messenger with password-stealing malware.
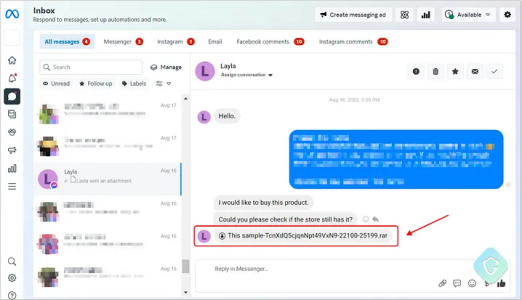
The attackers start by sending messages pretending to be copyright violations or requests for more information about a product. The message contains an attachment, usually a RAR/ZIP file, that runs a batch script containing the malware payload.
Scammers are tricking business owners into downloading the attachment, a Python-based stealer that takes all the passwords stored on the browser and then sends the stolen information back to the hackers via Telegram or Discord bot Application Programming Interface (API).
More than that, the malware also wipes the cookies from the victim’s device to log them out of their accounts. This gives the scammers time to change the passwords of the hijacked accounts.
Since social media companies can take a while to respond to emails about compromised accounts, the scammers have ample time to engage in fraudulent activities with those accounts.
This attack chain isn’t new, but the scale of the campaign is alarming—with roughly 100,000 attempts per week. Facebook users from Australia, North America, Europe, Japan and Southeast Asia are being targeted by this phishing campaign.
Guardio Labs also mentioned that 7 per cent of Facebook’s business accounts have been targeted, and 0.4 per cent of them downloaded the malicious file.
Furthermore, they reported that one in seventy accounts is ultimately compromised, resulting in a massive financial loss.
Here is the attack chain according to Guardio Labs:
The researchers have linked the campaign to Vietnamese hackers.
‘This python stealer reveals the Vietnamese origin of these threat actors,' Guardio revealed.
They noticed the strings in the malware and the use of ‘Coc Coc’ web browser in this campaign, which is popular in Vietnam.
‘The message "Thu Spam lần thứ" which is sent to the Telegram bot appended with a counter of execution time, translates from Vietnamese as "Collect Spam for the X time",’ they added.
In May 2023, Facebook announced it had disrupted a Vietnam-originated campaign that deployed a new info-stealer malware named 'NodeStealer'.
In April 2023, Guardio Labs reported again about a Vietnamese threat actor who abused Facebook's Ads service to infect approximately half a million users with info-stealing malware.

Members, it’s important to stay vigilant, especially regarding messages containing attachments.
If you’re ever suspicious, then it’s always a good idea to independently look into the message and message sender to make sure everything is legitimate.
Don’t forget, you can always access our Scam Watch forum, where members share stories and tips on how to avoid being victims of scams.
What do you think of this story, members? Have you encountered a similar message on Facebook? Share your experience in the comments below!
This is exactly what hackers have been doing, according to a worrying report from Guardio Labs. They’re using massive phishing networks and fake and/or compromised Facebook accounts to target vulnerable business owners via Messenger with password-stealing malware.
The attackers start by sending messages pretending to be copyright violations or requests for more information about a product. The message contains an attachment, usually a RAR/ZIP file, that runs a batch script containing the malware payload.
Scammers are tricking business owners into downloading the attachment, a Python-based stealer that takes all the passwords stored on the browser and then sends the stolen information back to the hackers via Telegram or Discord bot Application Programming Interface (API).
More than that, the malware also wipes the cookies from the victim’s device to log them out of their accounts. This gives the scammers time to change the passwords of the hijacked accounts.
Since social media companies can take a while to respond to emails about compromised accounts, the scammers have ample time to engage in fraudulent activities with those accounts.
This attack chain isn’t new, but the scale of the campaign is alarming—with roughly 100,000 attempts per week. Facebook users from Australia, North America, Europe, Japan and Southeast Asia are being targeted by this phishing campaign.
Guardio Labs also mentioned that 7 per cent of Facebook’s business accounts have been targeted, and 0.4 per cent of them downloaded the malicious file.
Furthermore, they reported that one in seventy accounts is ultimately compromised, resulting in a massive financial loss.
Here is the attack chain according to Guardio Labs:
The researchers have linked the campaign to Vietnamese hackers.
‘This python stealer reveals the Vietnamese origin of these threat actors,' Guardio revealed.
They noticed the strings in the malware and the use of ‘Coc Coc’ web browser in this campaign, which is popular in Vietnam.
‘The message "Thu Spam lần thứ" which is sent to the Telegram bot appended with a counter of execution time, translates from Vietnamese as "Collect Spam for the X time",’ they added.
In May 2023, Facebook announced it had disrupted a Vietnam-originated campaign that deployed a new info-stealer malware named 'NodeStealer'.
In April 2023, Guardio Labs reported again about a Vietnamese threat actor who abused Facebook's Ads service to infect approximately half a million users with info-stealing malware.
Key Takeaways
- Hackers are using a large network of fake and manipulated Facebook accounts to target business accounts with phishing messages on Facebook Messenger.
- The attackers trick victims into downloading a Python-based password-stealing malware, capable of grabbing cookies and passwords stored in the victim's browser. They can also delete the cookies, logging the victims out of their accounts.
- Guardio Labs reported that approximately 100K phishing messages are sent each week and approximately 7 per cent of all of Facebook's business accounts have been targeted.
- The Vietnamese-origin campaign has been linked to the attack due to specific strings in the malware and usage of the 'Coc Coc' web browser popular in Vietnam.
Members, it’s important to stay vigilant, especially regarding messages containing attachments.
If you’re ever suspicious, then it’s always a good idea to independently look into the message and message sender to make sure everything is legitimate.
Don’t forget, you can always access our Scam Watch forum, where members share stories and tips on how to avoid being victims of scams.
What do you think of this story, members? Have you encountered a similar message on Facebook? Share your experience in the comments below!